Security operations centers are under more pressure today than at any point in the last decade. Threat volume continues to rise, attack techniques evolve faster than playbooks can be updated, and business leaders expect near real time visibility into risk. At the same time, security teams are asked to do more with fewer resources, tighter budgets, and limited hiring options. These conditions have pushed SOC leaders to rethink how work gets done and how decisions are supported.
In this environment, AI SOC agents and platforms did not emerge as experimental technology. They appeared as a response to sustained operational strain. Teams needed help absorbing alerts, prioritizing work, and maintaining focus without burning out analysts. The conversation shifted from tools that generate more data to systems that reduce noise and support human judgment. As a result, AI supported SOC solutions began moving from curiosity to necessity.
What AI SOC agents mean for security teams
For most security teams, AI SOC agents represent a change in how work flows through the SOC rather than a replacement for analysts. These agents act as digital assistants that help manage volume, context, and pace. Instead of forcing analysts to manually triage thousands of alerts, teams can rely on AI support to surface what deserves attention first and what can safely wait.
The practical benefit is cognitive relief. Analysts spend less time jumping between dashboards and more time understanding incidents that matter. Over the course of a shift, that difference is significant. Decision fatigue drops, handoffs become cleaner, and fewer mistakes are made late in the day. For managers, AI SOC agents provide consistency in how work is handled, even when teams are stretched thin or operating across time zones.
Why SOC operations needed a new approach
Traditional SOC models were built for a different threat landscape. Alert volumes were lower, tools were fewer, and escalation paths were clearer. That structure no longer holds. Modern environments generate constant streams of alerts from cloud platforms, identity systems, endpoints, and third party services. Even well tuned tools produce more signals than human teams can reasonably process.
Staffing constraints make the problem worse. Experienced analysts are difficult to hire and expensive to retain. Junior staff require time and oversight, which pulls senior analysts away from high value work. Over time, teams become reactive rather than strategic. Burnout increases, turnover rises, and institutional knowledge is lost. Under these conditions, adding more tools only compounds the issue.
How AI assistance fits into modern SOC workflows
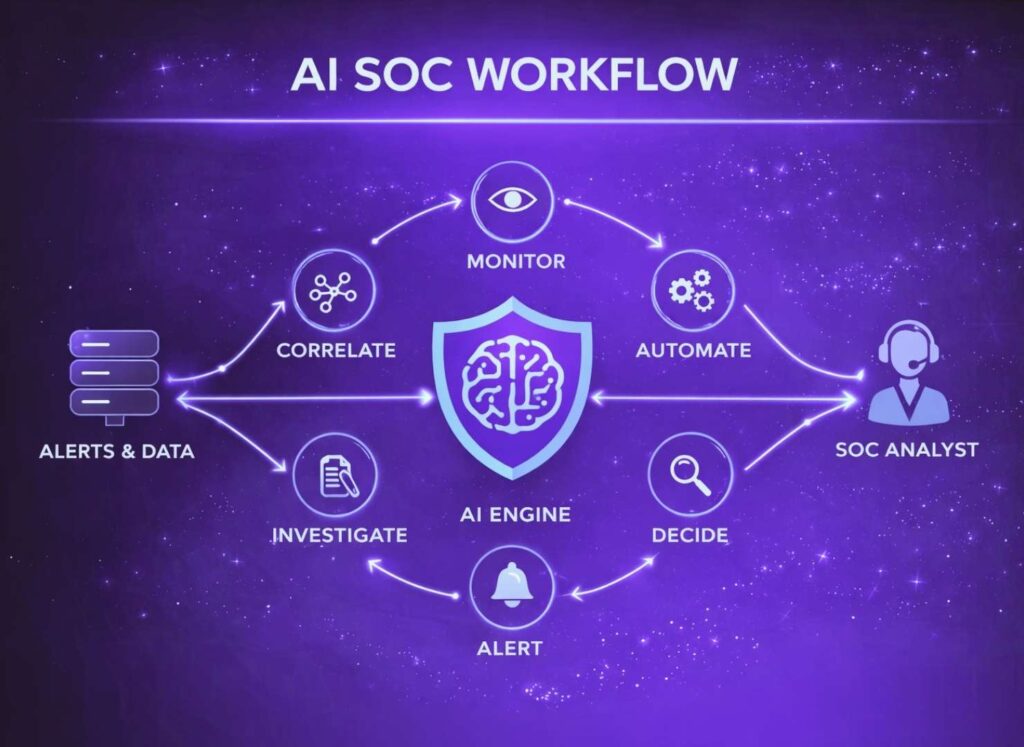
AI assistance fits best when it supports existing workflows rather than forcing teams to rebuild everything. In practice, this means helping with early stage tasks such as alert sorting, context gathering, and initial assessment. When these steps are handled consistently, analysts can engage incidents with better focus and less friction.
In many SOCs, AI support acts as a first pass reviewer that works continuously in the background. It prepares information, highlights patterns, and presents findings in a way that aligns with how teams already operate. The analyst remains in control, but the workload becomes more manageable. Over time, this support helps teams maintain quality even as alert volume grows.
Where organizations see the earliest impact
The earliest impact of AI SOC agents is usually felt in day to day efficiency. Teams notice faster triage times, fewer low value escalations, and improved shift handovers. Analysts report feeling more in control of their workload and less overwhelmed by noise. These gains often appear within weeks rather than months.
Management teams also benefit quickly. Reporting becomes more consistent, incident timelines are clearer, and leadership gains confidence that critical issues are not being missed. While long term strategic value develops over time, the initial improvements in focus and throughput are what drive early adoption. For organizations under constant operational pressure, that immediate relief is often the deciding factor.
Once AI SOC platforms moved beyond early experimentation, their real value became visible during live investigations. This is where pressure is highest and where small delays or missed context can change outcomes. Analysts are expected to make decisions quickly, explain those decisions clearly, and move incidents forward without losing sight of the bigger picture. AI support entered this phase not as a shortcut, but as a stabilizing layer inside daily SOC operations.
At this stage, the focus shifts away from why AI was adopted and toward how it supports work already happening on the SOC floor. The most effective platforms do not alter how analysts think. Instead, they reduce friction in the investigative process, helping teams maintain clarity when signal volume and time pressure collide.
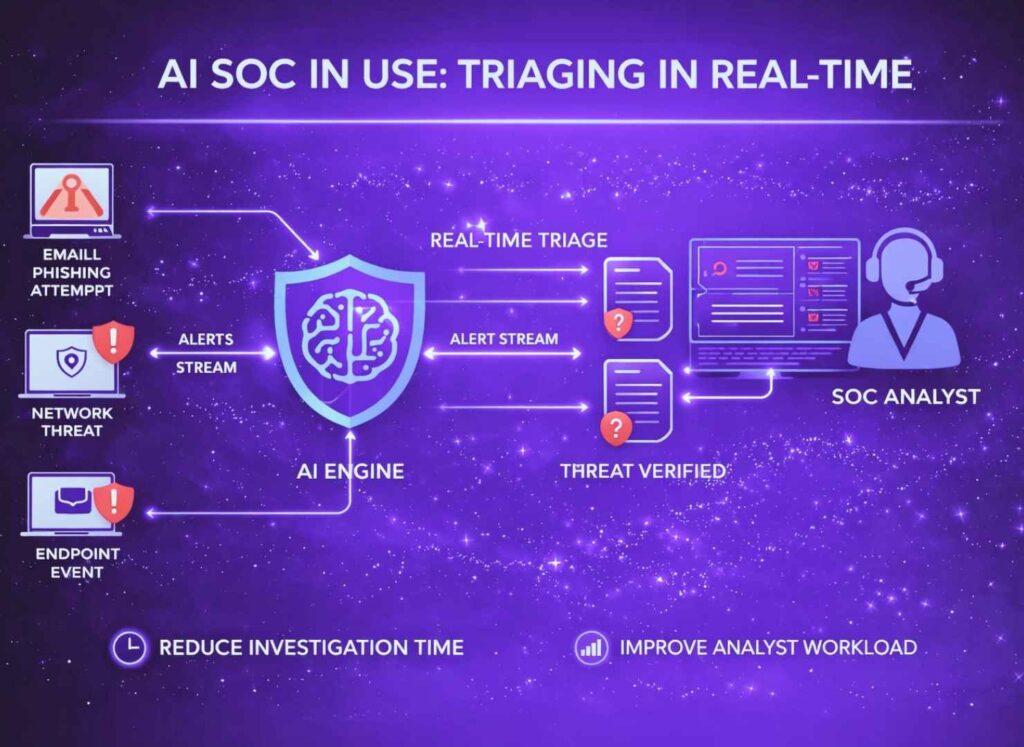
Alert intake and signal organization
The starting point for most investigations is still an alert, but the challenge lies in the sheer number arriving every hour. Modern SOCs receive signals from identity systems, endpoints, cloud services, email gateways, and external feeds. Even with tuning, analysts face a constant stream of notifications that compete for attention. AI SOC platforms help by organizing this intake before it reaches human review.
Rather than presenting alerts as isolated events, these systems group related signals into coherent units of work. Analysts see clusters instead of fragments, which immediately reduces noise. By organizing alerts based on shared users, assets, or time windows, platforms help teams focus on situations rather than individual triggers. This structure allows analysts to assess scope earlier and avoid chasing false leads that appear serious in isolation.
Context building across users and systems
Once an alert group is identified, the next challenge is understanding context. Analysts need to know who was involved, what systems were touched, and whether activity fits normal patterns or signals risk. Gathering this information manually often means pivoting across multiple tools and dashboards, which slows investigations and increases the chance of missed details.
AI SOC platforms assist by pulling relevant context into a single investigative view. User behavior, recent access history, system changes, and related alerts are presented together, allowing analysts to build a mental model quickly. Instead of assembling the story piece by piece, teams can focus on interpreting what they see. This consolidated context helps analysts understand not just what happened, but why it may have occurred.
Investigation support and decision guidance
As investigations progress, analysts must decide whether activity is benign, suspicious, or actively harmful. These decisions carry weight, especially when they trigger containment actions or executive communication. AI SOC platforms support this phase by highlighting patterns and sequences that matter, without dictating outcomes.
In practice, this means helping analysts see timelines clearly and understand how events connect. Platforms may surface similar past incidents, show how activity escalated over time, or point out deviations from expected behavior. The goal is not to replace judgment, but to ensure decisions are made with full awareness. Analysts remain responsible for conclusions, but they do not have to rely solely on memory or intuition under pressure.
Analyst control and human oversight
A critical requirement for SOC teams is maintaining control over investigations. Analysts need to trust the systems they use, especially when decisions affect production environments or sensitive data. Effective AI SOC platforms are designed to support oversight rather than obscure it. Actions, recommendations, and summaries are transparent and reviewable.
Human oversight remains central throughout the process. Analysts can validate findings, override suggestions, and adjust workflows based on experience and organizational context. This balance preserves accountability while still delivering efficiency gains. Over time, teams develop confidence in how AI support fits into their processes, not as an authority, but as a dependable assistant that enhances consistency and focus.
After initial evaluation and early success in investigations, the real test for AI SOC platforms begins with sustained operational use. Deploying a new layer into an already complex SOC environment requires careful planning, patience, and a clear understanding of how people actually work. Many organizations discover that technical readiness matters less than operational alignment. The difference between success and frustration often comes down to how well the platform fits existing processes and team culture.
At this stage, the conversation shifts toward integration, adoption, and measurement. Security leaders focus on minimizing disruption while extracting tangible value. Rather than seeking immediate transformation, teams that succeed treat AI SOC platforms as an incremental improvement to how work flows through the SOC.
Integrating AI SOC platforms into existing tools
Most SOCs operate with a dense stack of tools built over years. SIEM platforms, endpoint solutions, identity systems, and ticketing workflows are deeply embedded in daily operations. Introducing AI SOC platforms works best when they connect into this ecosystem rather than sitting alongside it as a separate interface. Analysts should not feel forced to abandon familiar workflows to gain value.
Successful integrations usually begin with limited scope. Teams connect the platform to a subset of data sources or focus on a specific alert category. This approach reduces risk and allows teams to observe behavior in real conditions. Over time, additional integrations are added based on demonstrated value. By aligning deployment with existing workflows, organizations reduce resistance and avoid unnecessary process redesign.
Building analyst trust and adoption
Trust determines whether AI assistance becomes part of daily work or remains underused. Analysts are naturally skeptical of new systems that claim to simplify complex investigations. That skepticism increases when recommendations lack transparency or context. Building trust requires showing how assistance supports, rather than challenges, analyst expertise.
Training plays a critical role in adoption. Instead of broad theoretical sessions, effective teams focus on scenario based walkthroughs tied to real incidents. Analysts learn how the platform behaves during investigations they recognize. Managers also reinforce adoption by encouraging feedback and adjusting usage guidelines based on analyst input. When teams feel heard, confidence grows and usage becomes more consistent.
Measuring operational value over time
Unlike traditional tools, the value of AI SOC platforms often appears gradually. Early metrics tend to focus on operational efficiency rather than prevention outcomes. Teams track changes in triage time, alert volume handled per analyst, and investigation throughput. These measures provide tangible signals that workflows are improving.
Over longer periods, organizations begin to observe secondary benefits. Fewer escalations stall, documentation quality improves, and handovers between shifts become smoother. Leadership gains clearer visibility into SOC activity without demanding constant manual reporting. By reviewing these trends regularly, teams can adjust deployment focus and ensure the platform continues to support evolving priorities.
Common challenges and practical lessons
Despite careful planning, challenges are common. One frequent issue is attempting to deploy too broadly too quickly. When platforms are introduced across all alert types at once, analysts can feel overwhelmed and disengaged. Gradual rollout allows teams to adapt and refine usage patterns before expanding scope.
Another challenge involves unclear ownership. Without defined responsibility for configuration, tuning, and review, platforms can drift from operational needs. Successful SOCs assign clear ownership while maintaining collaborative input. They treat AI SOC platforms as living systems that evolve with the environment, not static tools installed and forgotten.
Appendix: AI SOC Platforms and Solutions
The following platforms are identified through independent market observation and sustained industry presence across enterprise and mid market security operations. This list is illustrative rather than exhaustive and does not imply ranking or endorsement. Each entry is presented using a consistent structure to support reference and comparison.
| Company | Key Features | Use Cases | Notable Strength |
|---|---|---|---|
| GuruCul AI SOC | Behavioral analytics, anomaly detection, investigation assistance | Insider threat detection, complex user behavior investigations | Deep behavioral context that reduces alert noise |
| AiStrike | Alert triage, SIEM and EDR integration | Day to day SOC investigations | Practical fit for lean security teams |
| Intezer | Code level analysis, malware lineage tracking | Malware triage, forensic investigations | Strong forensic clarity for binary analysis |
| 7AI | Multi agent orchestration, SOC task automation | High volume alert handling, workflow automation | Coordinated agent based SOC execution |
| SentinelOne Purple AI | Investigation summaries, response guidance | Endpoint driven incident response | Tight integration with XDR workflows |
| CrowdStrike Charlotte AI | Alert prioritization, contextual investigation | Enterprise scale SOC operations | Strong endpoint context at scale |
| BlinkOps | Autonomous playbooks, response orchestration | Automated remediation workflows | Flexible security automation design |
| Bricklayer AI | Lightweight triage agents, signal reduction | Initial alert analysis | Fast time to value for smaller SOCs |
| Conifers.ai | Cloud visibility, AI correlation | Cloud environment monitoring | Cloud focused operational clarity |
| Vectra AI | Network and identity threat detection | Lateral movement and identity abuse | Strong identity threat prioritization |
| Dropzone AI | Autonomous investigations, evidence collection | High alert volume environments | Reduces analyst investigation load |
| Exaforce | AI assisted analytics, SIEM optimization | Large scale log analysis | Cost efficient SIEM investigation |
| Legion Security | Learn from analyst actions, workflow consistency | Repeatable triage processes | Human informed automation logic |
| Prophet Security | Agentic alert resolution, prediction | Automated alert handling | Reduced manual SOC workload |
| Qevlar AI | Evidence backed reasoning, triage support | Analyst decision validation | Transparent investigation logic |
| Radiant Security | Autonomous triage and response | SOC scaling without staff growth | Consistent response execution |
| Mindgard | AI model risk monitoring, red teaming | AI system security oversight | Specialized AI risk visibility |
| Rapid7 | AI triage, MDR integration | Hybrid tool and managed SOCs | Strong operational coverage |
| Abnormal Security | Behavioral email threat detection | Social engineering investigations | High accuracy email attack detection |
| Arctic Wolf | Managed SOC, AI enrichment | 24×7 monitoring and response | Operational maturity with low overhead |
| Microsoft Security Copilot | Incident summaries, workflow assistance | Microsoft centric SOC operations | Broad security ecosystem integration |
GuruCul AI SOC
Platform approach
Behavior driven AI SOC platform focused on advanced anomaly detection and investigation support across diverse security environments.
SOC assistance focus
Alert prioritization, investigation context, and analyst decision support during complex user and entity based incidents.
Typical environments
Enterprises with mature SOCs, high identity activity, and complex insider or behavioral risk exposure.
AiStrike
Platform approach
AI SOC platform built for mid market security teams with SIEM and EDR integrations.
SOC assistance focus
Alert triage, investigation support, and analyst workload reduction.
Typical environments
Lean SOC teams managing enterprise grade tools with limited staffing.
Intezer
Platform approach
Forensic AI SOC platform centered on code level analysis and malware lineage tracking.
SOC assistance focus
Malware investigation, alert validation, and forensic clarity for suspicious binaries and behaviors.
Typical environments
Enterprise SOCs handling frequent malware alerts and incident response investigations.
7AI
Platform approach
Multi agent AI SOC platform designed around orchestrated automation and autonomous task execution.
SOC assistance focus
End to end alert handling, agent coordination, and SOC workflow automation.
Typical environments
Organizations seeking scalable SOC automation across large alert volumes.
SentinelOne Purple AI
Platform approach
AI driven SOC assistance embedded within the Singularity XDR platform.
SOC assistance focus
Investigation summaries, alert interpretation, and response workflow support.
Typical environments
Endpoint heavy environments with XDR centered SOC operations.
CrowdStrike Charlotte AI
Platform approach
AI assisted investigation and response within the Falcon security platform.
SOC assistance focus
Alert triage, contextual investigation, and analyst efficiency.
Typical environments
Large enterprises operating cloud native endpoint focused SOCs.
BlinkOps
Platform approach
AI powered security automation platform emphasizing autonomous playbooks.
SOC assistance focus
Response automation, workflow orchestration, and operational scale.
Typical environments
SOCs prioritizing automation across detection and response activities.
Bricklayer AI
Platform approach
Lightweight multi agent SOC platform focused on alert triage efficiency.
SOC assistance focus
Initial investigation, signal reduction, and analyst task delegation.
Typical environments
Small to mid sized SOCs seeking rapid triage improvements.
Conifers.ai
Platform approach
Cloud native SOC platform emphasizing visibility and correlation across cloud services.
SOC assistance focus
Alert correlation, investigation context, and cloud environment clarity.
Typical environments
Cloud first organizations with distributed infrastructure.
Vectra AI
Platform approach
AI powered threat detection across network and identity activity.
SOC assistance focus
Threat prioritization and investigation guidance for lateral movement and identity abuse.
Typical environments
Hybrid enterprises with strong identity dependency.
Dropzone AI
Platform approach
Autonomous AI SOC analyst platform designed for alert investigation.
SOC assistance focus
Alert analysis, investigation summaries, and evidence collection.
Typical environments
SOCs managing high alert volumes with limited analyst capacity.
Exaforce
Platform approach
AI assisted security analytics platform focused on SIEM efficiency.
SOC assistance focus
Investigation acceleration and cost reduction through analytics optimization.
Typical environments
Organizations optimizing large scale SIEM deployments.
Legion Security
Platform approach
AI SOC platform that learns automation logic from analyst behavior.
SOC assistance focus
Consistent triage and investigation workflows informed by human expertise.
Typical environments
SOCs emphasizing analyst led process refinement.
Prophet Security
Platform approach
Agentic AI SOC platform focused on automated alert resolution.
SOC assistance focus
Alert handling, investigation automation, and resolution guidance.
Typical environments
Security teams aiming to reduce manual triage effort.
Qevlar AI
Platform approach
AI investigation copilot focused on evidence backed alert triage.
SOC assistance focus
Investigation reasoning, alert validation, and decision support.
Typical environments
SOC teams requiring transparent investigation justification.
Radiant Security
Platform approach
Agentic AI SOC platform for triage and response automation.
SOC assistance focus
Alert handling consistency and response coordination.
Typical environments
Enterprises scaling SOC operations without expanding staff.
Mindgard
Platform approach
AI security platform focused on model protection and AI risk management.
SOC assistance focus
AI system monitoring and integration into broader SOC workflows.
Typical environments
Organizations deploying AI models in production environments.
Rapid7
Platform approach
AI assisted detection and response integrated with managed services.
SOC assistance focus
Alert triage, investigation support, and response prioritization.
Typical environments
Mid to enterprise SOCs combining tools and MDR support.
Abnormal Security
Platform approach
Behavioral AI platform focused on email threat detection.
SOC assistance focus
Investigation context for social engineering and account compromise.
Typical environments
Enterprises with high email based threat exposure.
Arctic Wolf
Platform approach
Managed SOC platform with AI driven enrichment and analysis.
SOC assistance focus
Incident triage, investigation support, and continuous monitoring.
Typical environments
Mid market organizations with limited internal SOC resources.
Microsoft Security Copilot
Platform approach
AI assisted SOC workflows embedded across Microsoft security products.
SOC assistance focus
Incident summarization, investigation guidance, and operational visibility.
Typical environments
Organizations standardized on Microsoft security and cloud platforms.


