What modern SIEM platforms are
Modern Security Information and Event Management platforms, commonly called SIEM, are centralized security systems designed to give organizations a single, trusted view of what is happening across their digital environment. They collect security related information from many sources and present it in a way that helps teams understand risk, spot threats, and respond with confidence.
At a high level, a modern SIEM acts as the security nerve center of an organization. Instead of teams checking many tools and dashboards, SIEM brings signals together into one place. This shared visibility allows both technical teams and business leaders to make informed decisions based on the same data.
Unlike earlier generations, today’s SIEM platforms are built for speed, scale, and clarity. They are designed to operate in environments that include cloud services, remote work, mobile users, and third-party platforms, all of which generate massive volumes of security data every day.

How SIEM evolved from log management
The roots of SIEM go back to basic log management. Early security teams stored system logs mainly for troubleshooting or compliance. Over time, attackers became more advanced, and simple log storage was no longer enough.
Traditional SIEM tools emerged to centralize logs and apply fixed rules to detect known threats. While this approach improved visibility, it struggled as environments grew more complex. Data volumes increased sharply, alerts became noisy, and teams found it difficult to separate real risks from routine activity.
Next generation SIEM platforms evolved in response to these pressures. The focus shifted from storing logs to providing actionable insight. Modern platforms aim to reduce manual effort, highlight what matters most, and support faster decision making without overwhelming users.
The business and security problems SIEM solves
Organizations adopt SIEM because it addresses several persistent challenges that affect both security and business operations.
First, visibility is fragmented in most environments. Applications, networks, users, and devices all generate data in different places. SIEM reduces blind spots by offering a centralized view, which is essential for understanding exposure and identifying suspicious activity early.
Second, security teams face alert fatigue. When every tool raises alarms independently, teams waste time chasing low risk issues. A modern SIEM helps prioritize concerns so attention is focused on events that could have real impact.
Third, many organizations must meet regulatory and audit requirements. SIEM supports this need by maintaining consistent records of security activity, access events, and incident responses, all in one system.
Finally, leadership needs reliable insight into risk. Executives and board members are expected to make decisions about investment, insurance, and response planning. SIEM provides structured, defensible information that supports these discussions.
Who uses SIEM and why
SIEM platforms are used across multiple roles, not only within the security team.
Security Operations Center teams rely on SIEM to monitor activity, investigate incidents, and coordinate responses. For them, SIEM is the primary workspace where daily security operations take place.
IT and infrastructure teams use SIEM to understand system behavior and identify operational issues that may have security implications. This shared visibility helps reduce friction between IT and security functions.
Compliance and risk teams depend on SIEM for evidence. Whether preparing for audits or internal reviews, they need consistent and searchable records of security controls and events.
Executive leadership benefits from SIEM at a strategic level. Dashboards and summaries provide a clear picture of organizational risk, trends over time, and the effectiveness of security investments.
High level comparison to legacy tools
Legacy security tools were often designed to solve narrow problems. Firewalls focused on network traffic, endpoint tools focused on devices, and log systems focused on storage. Each tool offered value but required manual correlation.
Modern SIEM platforms aim to unify these perspectives. Rather than replacing every security control, SIEM sits above them, connecting signals into a coherent story. This shift reduces dependency on human intuition alone and improves consistency in how threats are identified and managed.
Another key difference is adaptability. Older systems were rigid and difficult to tune as environments changed. Next gen SIEM platforms are designed to grow with the organization, supporting new technologies, users, and business models without constant reengineering.
Centralized visibility explained simply
Centralized visibility does not mean collecting everything without purpose. It means ensuring that security relevant information can be seen together, in context.
For example, a single user action might touch a cloud application, a corporate network, and a mobile device. Viewed separately, each event appears normal. Viewed together, the pattern may indicate risk. SIEM enables this broader perspective without requiring teams to manually connect the dots.
This unified view also improves communication. When everyone looks at the same source of truth, discussions become clearer and decisions are made faster.
Rule based versus behavior driven detection at a high level
At a conceptual level, traditional SIEM relied heavily on predefined rules. These rules worked well for known threats but struggled with new or subtle attacks.
Modern SIEM platforms balance rules with more adaptive approaches. Instead of only asking whether an event matches a fixed condition, they look for unusual patterns or changes over time. This high-level shift allows organizations to detect risks that do not follow predictable paths.
It is important to note that this discussion remains conceptual. The goal for leadership is not to understand how detection works internally, but to understand that modern SIEM is better suited to today’s dynamic threat landscape.
Scalability and cloud relevance
Digital environments are no longer static. Organizations add cloud services, onboard partners, and support remote workforces at a rapid pace. Security systems must scale without slowing the business.
Next gen SIEM platforms are built with this reality in mind. They are designed to handle growth in data volume and user activity while maintaining performance and clarity. This scalability supports innovation by reducing security friction when new initiatives are launched.
Cloud relevance also means accessibility. Teams can access insights securely from anywhere, supporting distributed operations and global organizations.
Strategic value for leadership and SOC teams
For security teams, SIEM improves daily effectiveness by reducing noise, improving context, and supporting faster response. This leads to better outcomes with the same or fewer resources.
For leadership, SIEM offers confidence. Decisions about risk tolerance, investment, and response planning are grounded in evidence rather than assumptions. Over time, this alignment between technical reality and business strategy strengthens organizational resilience.
Why organizations need next gen SIEM today
Threats are faster, environments are more complex, and expectations are higher than ever. Organizations can no longer rely on fragmented tools and manual processes to protect critical assets.
Next generation SIEM platforms address this gap by providing clarity, consistency, and strategic insight. They help organizations move from reactive security to informed risk management, which is essential in today’s digital landscape.
This foundation explains why SIEM remains a core pillar of modern security programs and why its evolution continues to matter at every level of the organization.
Core Concepts and Capabilities
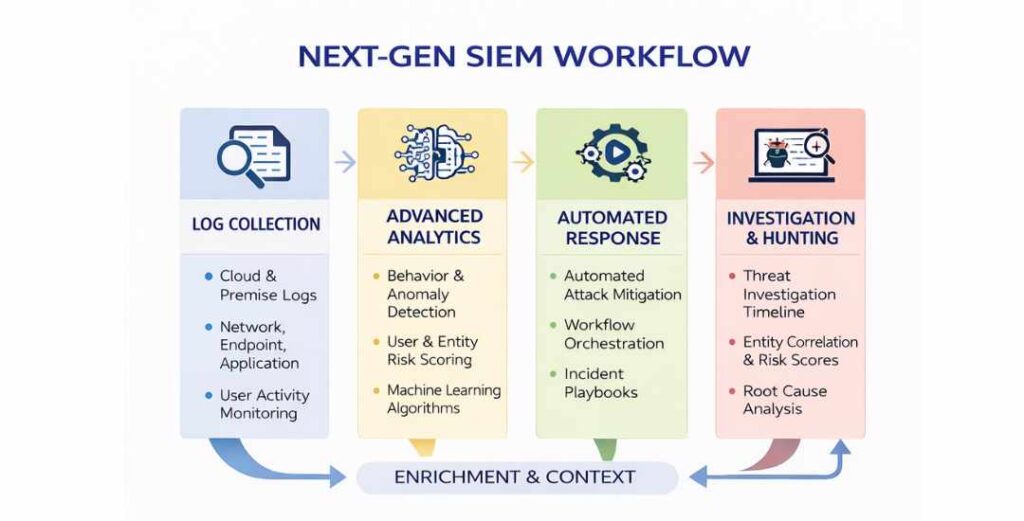
How data flows through a modern SIEM
A next generation SIEM works by moving data through a structured and continuous process. First, it ingests data from many sources such as endpoints, servers, identity systems, cloud platforms, and network tools. These sources produce events in different formats, at different speeds, and with different levels of detail.
Once ingested, the SIEM normalizes this data. Normalization means converting raw events into a common structure so they can be analyzed together. Without this step, comparing activity across systems would be unreliable and inefficient. Normalized data allows the platform to understand that a login event, a file access event, and a network connection may all relate to the same user or system.
After normalization, the data is stored and made available for analysis. At this stage, the SIEM begins to evaluate activity over time rather than as isolated moments.
Behavioral analytics and baselining
One of the defining capabilities of a next gen SIEM is behavioral analytics. Instead of only checking whether an action matches a known rule, the platform learns what normal activity looks like for users, devices, and systems.
Behavior baselining works by observing patterns over days or weeks. For example, it may learn when a user usually logs in, which systems they access, and how much data they typically move. This baseline becomes a reference point.
When activity deviates from this learned pattern, the SIEM flags it for closer review. A login at an unusual time, access to a new system, or a sudden spike in activity may not be malicious on its own. However, when combined with other deviations, it can signal risk.
This approach is especially useful for detecting insider threats and compromised accounts, where activity often appears legitimate at first glance.
Event correlation versus isolated alerts
Traditional security tools generate alerts based on single events. A failed login, a blocked connection, or a configuration change may each trigger an alert on its own.
Next generation SIEM platforms focus on correlation. Correlation means linking related events across time and systems to form a complete narrative. Instead of treating alerts as separate issues, the SIEM asks how they connect.
For example, a sequence of events such as a suspicious login, followed by privilege changes, and then unusual data access may indicate account compromise. Each event alone may seem low risk, but together they form a meaningful pattern.
Correlation reduces noise by grouping related activity into a single investigation. This helps analysts focus on true threats rather than chasing hundreds of disconnected alerts.
Risk scoring and prioritization
Modern SIEM platforms assign risk scores to users, systems, or sessions based on observed behavior. Risk scoring combines multiple signals into a single measure of concern.
The score increases when risky actions occur and decreases when activity returns to normal. This dynamic view allows analysts to see which entities deserve immediate attention.
Risk scoring is critical for handling long running attacks. Some threats unfold slowly over weeks, staying below alert thresholds. By tracking cumulative risk, the SIEM can surface these attacks before damage occurs.
This capability improves analyst efficiency by directing effort toward the most concerning activity instead of the loudest alerts.
Machine learning in practical terms
Machine learning in SIEM is not about replacing analysts. It is about assisting them by handling scale and complexity.
At a practical level, machine learning helps identify patterns that are difficult to define with static rules. It can detect subtle changes in behavior, group similar events, and adapt as environments evolve.
Importantly, effective SIEM platforms apply machine learning with constraints. Models are trained on relevant security data and evaluated continuously to avoid false positives. The goal is consistent signal quality, not experimental automation.
This measured use of machine learning is one reason next gen SIEM platforms produce fewer but more meaningful alerts.
Context enrichment and why it matters
Raw events lack context. A login attempt means little without knowing who the user is, where they usually work, and what they are allowed to access.
Context enrichment adds this missing information. The SIEM enriches events with details such as user roles, device ownership, asset value, and known threat indicators. This enrichment happens automatically as data flows through the system.
With context, analysts can answer critical questions quickly. Is this system sensitive? Is this user privileged? Has this IP address been seen in past incidents?
Context turns data into insight and shortens investigation time significantly.
Automation and response support
Next generation SIEM platforms support automation to reduce repetitive manual work. Automation may include grouping related events, tagging known benign activity, or triggering predefined actions when risk thresholds are reached.
Automation does not mean acting blindly. Instead, it assists analysts by handling routine steps so they can focus on judgment and decision making.
For example, when a potential account compromise is detected, the SIEM may automatically gather recent activity, related systems, and historical behavior into one view. This preparation speeds up response without removing human oversight.
Analyst workflows and investigation tools
A modern SIEM is designed around analyst workflows. Dashboards provide high level visibility, showing current risk levels, active investigations, and trends over time.
When an alert is opened, investigation tools allow analysts to pivot easily. They can move from a user to related systems, from a system to recent activity, and from events to timelines without switching tools.
Timelines are especially important. They show how an incident unfolded step by step, making it easier to understand attacker behavior and decide next actions.
These workflows are essential for detecting lateral movement, where attackers move quietly across systems after initial access.
Detecting complex and long running attacks
Next gen SIEM platforms excel at detecting attacks that unfold slowly or involve multiple stages. Insider threats, lateral movement, and advanced account compromise often rely on blending in with normal activity.
By combining behavioral baselines, correlation, risk scoring, and context enrichment, the SIEM can surface these threats even when no single action is clearly malicious.
This capability is what separates next generation platforms from earlier tools that focused only on immediate alerts.
What makes a SIEM truly next generation
A SIEM becomes truly next generation when it moves beyond collecting data and starts delivering understanding. The ability to process diverse data, learn normal behavior, connect events, and support efficient investigations defines modern SIEM capability.
These internal concepts and technologies are the foundation that enable security teams to operate effectively in complex environments. They explain how next gen SIEM platforms work beneath the surface and why they are central to modern security operations.
Evaluation, Adoption, and Real-World Usage
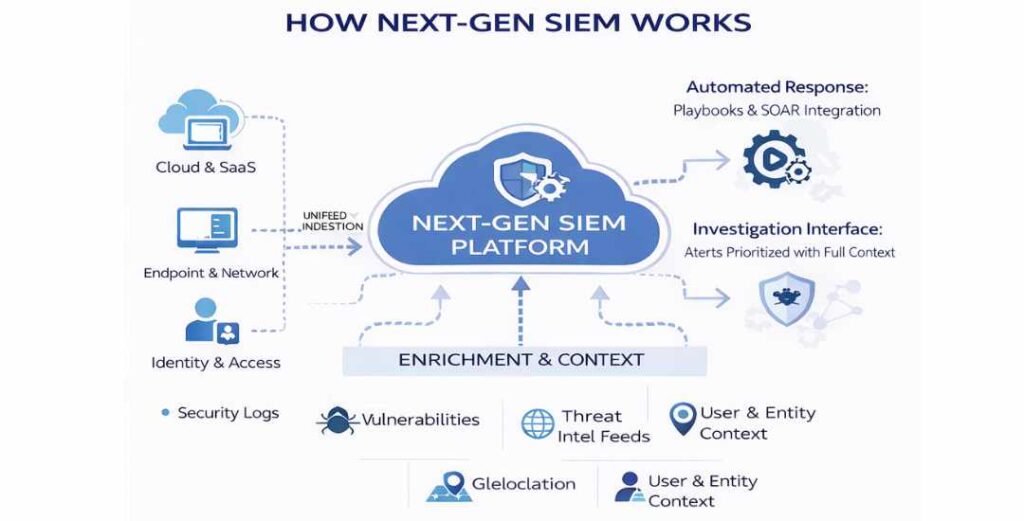
How organizations evaluate SIEM platforms
When organizations evaluate a modern SIEM platform, the process usually starts with operational needs rather than technology features. Security leaders ask practical questions. Can this platform handle our data volume? Will it fit into how our SOC already works? Can it grow as the organization changes?
Selection criteria often focus on flexibility, scalability, and usability. Teams look for platforms that can ingest data from existing tools without major rework. They also assess how easily analysts can navigate dashboards, investigate alerts, and collaborate during incidents.
Another important factor is operational alignment. A SIEM that looks powerful in demonstrations may fail if it does not match the skill level or structure of the SOC. Successful evaluations involve analysts, engineers, and leadership early so expectations are realistic and shared.
Planning deployment the right way
Deployment is one of the most critical phases in SIEM adoption. Many challenges arise when organizations try to deploy too much, too fast.
A common best practice is phased deployment. Instead of connecting every possible data source on day one, teams start with high value sources such as identity systems, core servers, and critical applications. This approach allows the SOC to learn the platform while maintaining control over alert volume.
Clear ownership is also essential. Deployment should not be treated as a one time technical project. It requires ongoing coordination between security, IT, and sometimes cloud or application teams. Defined roles help avoid gaps and confusion during rollout.
Integration planning across the environment
Effective SIEM usage depends on thoughtful integration planning. Each data source should have a clear purpose. Teams should ask why a source is being added and what questions it helps answer.
Identity systems are often a priority because user activity connects many security events. Cloud platforms, endpoints, and network tools usually follow. Integrations should be tested incrementally to ensure data quality before expanding coverage.
Poor integration planning can overwhelm analysts with low value data. Good planning keeps the SIEM focused on visibility that supports investigation and response.
Cloud, hybrid, and operational considerations
Many organizations operate in hybrid environments that include on premises systems and cloud services. SIEM deployment must reflect this reality.
Cloud based deployments offer flexibility and easier scaling, while hybrid approaches may be required for regulatory or operational reasons. The key is consistency. Analysts should experience the SIEM as a single system, regardless of where data originates.
Connectivity, access controls, and data retention policies should be addressed early. These decisions affect daily operations and long term sustainability.
Tuning for operational effectiveness
Tuning is not about changing algorithms. It is about aligning the SIEM with real world activity.
Early tuning efforts usually focus on reducing noise. Analysts review alerts to identify patterns that are consistently benign and adjust workflows accordingly. Over time, tuning becomes more strategic, helping the SIEM highlight activity that truly matters.
Successful organizations treat tuning as an ongoing process. As the environment changes, the SIEM must evolve with it. Regular reviews prevent alert fatigue and maintain trust in the platform.
SOC workflow adoption
A SIEM only delivers value when it becomes part of daily SOC workflows. This requires training, clear procedures, and leadership support.
Dashboards should reflect how analysts work, not just what data is available. Alert queues should align with triage processes. Investigation views should support handoffs between shifts.
Adoption improves when analysts see faster investigations and fewer distractions. Early wins build confidence and encourage deeper use of the platform.
Improving alert triage and response coordination
One of the most visible benefits of SIEM adoption is improved alert triage. Instead of reacting to isolated alerts, analysts work with grouped investigations that provide context.
This clarity improves response coordination. Teams can communicate findings more effectively, escalate incidents with confidence, and involve stakeholders with accurate information.
Clear timelines and shared views reduce friction during high pressure incidents and help organizations respond with consistency.
Measuring success in practice
Measuring SIEM success goes beyond counting alerts. Mature organizations track operational outcomes such as reduced investigation time, fewer false positives, and faster incident containment.
Other indicators include analyst satisfaction, consistency in response processes, and improved visibility into risk trends. These metrics help leadership understand whether the SIEM supports strategic goals.
Measurement should be ongoing. Regular reviews allow teams to adjust priorities and demonstrate value over time.
Building long term security maturity
SIEM adoption is not an endpoint. It is part of a broader security maturity journey.
Early stages focus on visibility and basic response. As maturity grows, organizations use SIEM insights to refine processes, improve collaboration, and support proactive risk management.
Over time, the SIEM becomes a central system of record for security operations. It supports learning, accountability, and continuous improvement.
Using SIEM successfully in the real world
Organizations succeed with SIEM when they approach it as an operational capability rather than a technical tool. Careful evaluation, phased deployment, thoughtful integration, and continuous tuning are the foundations of success.
By aligning the platform with SOC workflows and measuring real outcomes, organizations turn SIEM into a practical asset that strengthens security operations over the long term.
Appendix: SIEM Company Highlights
| Company / Platform | Platform Focus | Primary Capabilities | Typical Use Cases |
|---|---|---|---|
| Gurucul – Next-Gen SIEM | Behavior-driven detection emphasizing context, risk accumulation, and reduced alert noise | Advanced behavioral analytics, risk scoring, investigation timelines, entity enrichment | High-fidelity threat detection, insider risk analysis, long-running attack discovery in enterprise SOCs |
| Splunk – Enterprise Security | Log-centric visibility built on large-scale data indexing and search | High-volume ingestion, correlation searches, customizable dashboards, broad integrations | Large enterprises with complex, data-heavy SOC environments |
| Fortinet – FortiSIEM | Infrastructure-centric monitoring spanning network, device, and performance data | Asset discovery, event correlation, performance monitoring, unified IT and security visibility | Organizations managing large network and hybrid infrastructures |
| Securonix – Unified Defense SIEM | Behavior-first analytics across cloud and on-prem environments | Risk scoring, behavioral baselining, threat content, investigation workflows | Insider threat detection, account compromise analysis, advanced behavioral monitoring |
| CrowdStrike – Falcon Next-Gen SIEM | Endpoint- and identity-informed monitoring on a cloud-native telemetry foundation | Real-time ingestion, endpoint and identity correlation, unified investigations | Organizations invested in EDR seeking broader visibility |
| Microsoft – Sentinel | Cloud-native SIEM centered on cloud services and identity | Scalable ingestion, analytics rules, automation playbooks, native cloud integrations | Cloud-first and hybrid organizations |
| IBM – Security QRadar SIEM | Event- and flow-based monitoring with offense-driven workflows | Event correlation, network flow analysis, offense prioritization | Established SOCs in regulated industries |
| Exabeam – SIEM | User-centric threat detection with session-based investigations | Behavioral baselining, risk scoring, timeline reconstruction | Insider threat visibility and account misuse detection |
| LogRhythm – SIEM | Integrated SOC platform combining detection, response, and case management | Correlation rules, investigation workflows, automated response | Mid to large enterprises seeking structured SOC operations |
| Rapid7 – InsightIDR | Cloud-delivered SIEM focused on speed and simplicity | UEBA, endpoint telemetry, guided investigations | Lean SOC teams and cloud-heavy environments |
| Logpoint – SIEM | Compliance-aware SIEM balancing security and regulatory needs | Log management, correlation, investigation tools, compliance reporting | Regulated sectors requiring audit readiness |
| Elastic – Elastic Security | Search-driven security analytics on an open data platform | High-speed search, flexible ingestion, detection rules, visual analysis | Technical teams needing customizable analytics |
| SolarWinds – Security Event Manager | Infrastructure-focused log and event monitoring | Event correlation, alerts, log analysis, basic automation | IT-centric teams managing on-prem infrastructure |
| ManageEngine – ADAudit Plus | Identity-centric monitoring for directory services | User change tracking, access auditing, reporting | Identity governance and audit preparedness |
| Exabeam – Fusion | Unified SIEM, automation, and investigation workflows | Behavior analytics, playbooks, case management | SOCs seeking integrated detection and response |
| OpenText – Enterprise Security Manager | Log-centric SIEM with structured correlation and long retention | Event normalization, correlation, investigation, compliance | Large organizations with mature SOC processes |
| Sumo Logic – SaaS Log Analytics | Cloud-native analytics with security monitoring | Scalable log analytics, detection rules, dashboards | Cloud-first distributed application environments |
| Graylog – Security | Open and extensible log analysis platform | Log aggregation, search, alerting, customizable content | Teams wanting flexible, self-managed analytics |
| AT&T Cybersecurity – SIEM | Network-informed monitoring influenced by telecom scale | Event correlation, network visibility, investigations | Enterprises with complex, high-traffic networks |
| Devo – Security Analytics Platform | High-performance real-time analytics at scale | Fast ingestion, long-term retention, interactive investigation | Large SOCs handling massive event volumes |
The following SIEM platforms are included based on independent industry research, analyst coverage, and observable market adoption across enterprise and mid-market environments. This appendix is designed as a reference section that complements the main article by illustrating how different SIEM platforms approach security monitoring and operations in practice.
The list is illustrative rather than exhaustive and does not imply ranking, preference, or endorsement. Each platform reflects a distinct design philosophy, operational emphasis, or deployment model that has influenced how it is commonly used in real-world security programs.
The entries below highlight differences in platform focus, core strengths, and typical usage patterns, helping readers understand the diversity of approaches within the SIEM landscape.
Gurucul Next-Gen SIEM
Platform focus
Designed around behavior-driven detection with an emphasis on analytical depth and reduced alert noise. The platform prioritizes context and risk accumulation over isolated event analysis.
Primary capabilities
Advanced behavioral analytics, risk-based scoring, investigation timelines, and enrichment across user and entity activity. Strong emphasis on analyst-led investigations.
Typical use cases
Organizations seeking high-fidelity threat detection, insider risk visibility, and long-running attack identification within enterprise SOC environments.
Splunk Enterprise Security
Platform focus
Log-centric visibility built on large-scale data indexing and search. The platform emphasizes flexibility and customization across diverse data sources.
Primary capabilities
High-volume data ingestion, correlation searches, customizable dashboards, and integration with a broad ecosystem of security tools.
Typical use cases
Large enterprises with complex environments, data-heavy SOCs, and teams requiring deep customization and analytics flexibility.
Fortinet FortiSIEM
Platform focus
Infrastructure-centric monitoring with strong emphasis on network, device, and performance visibility alongside security events.
Primary capabilities
Asset discovery, event correlation, performance monitoring, and unified visibility across network and security operations.
Typical use cases
Organizations managing large network infrastructures, hybrid environments, and security teams closely aligned with IT operations.
Securonix Unified Defense SIEM
Platform focus
Behavior-first analytics with a strong emphasis on user and entity behavior modeling across cloud and on-premises environments.
Primary capabilities
Risk scoring, behavioral baselining, threat detection content, and investigation workflows designed for complex attack scenarios.
Typical use cases
Enterprises focused on insider threat detection, account compromise analysis, and advanced behavioral monitoring.
CrowdStrike Falcon Next-Gen SIEM
Platform focus
Endpoint and identity-informed monitoring built on a cloud-native security telemetry foundation.
Primary capabilities
Real-time data ingestion, correlation across endpoint and identity signals, and integrated investigation views.
Typical use cases
Organizations heavily invested in endpoint detection platforms seeking unified visibility across user and device activity.
Microsoft Sentinel
Platform focus
Cloud-native SIEM designed for environments centered on cloud services and identity-driven operations.
Primary capabilities
Scalable data ingestion, analytics rules, automation playbooks, and native integration with cloud identity and workloads.
Typical use cases
Cloud-first organizations, hybrid environments, and teams operating within cloud-centric security ecosystems.
IBM Security QRadar SIEM
Platform focus
Event and flow-based monitoring with structured correlation and offense-based investigation models.
Primary capabilities
Event correlation, network flow analysis, offense prioritization, and mature investigation tooling.
Typical use cases
Established SOCs in regulated industries requiring structured workflows and predictable operational models.
Exabeam SIEM
Platform focus
User-centric threat detection emphasizing behavior analytics and session-based investigation.
Primary capabilities
Behavioral baselining, risk scoring, timeline reconstruction, and analyst-focused investigation views.
Typical use cases
Organizations prioritizing insider threat visibility, account misuse detection, and streamlined SOC investigations.
LogRhythm SIEM
Platform focus
Integrated security operations platform combining detection, response, and case management.
Primary capabilities
Correlation rules, investigation workflows, automated response actions, and centralized case handling.
Typical use cases
Mid to large enterprises seeking an all-in-one SOC platform with structured operational processes.
Rapid7 InsightIDR
Platform focus
Cloud-delivered SIEM with emphasis on rapid deployment and operational simplicity.
Primary capabilities
User behavior analytics, endpoint telemetry ingestion, threat detection, and guided investigations.
Typical use cases
Lean SOC teams, cloud-heavy organizations, and security programs focused on fast time to value.
Logpoint SIEM
Platform focus
Compliance-aware SIEM with a balance between security monitoring and regulatory reporting.
Primary capabilities
Log management, correlation, investigation tools, and built-in compliance content.
Typical use cases
Organizations in regulated sectors requiring clear audit trails alongside threat detection.
Elastic Security
Platform focus
Search-driven security analytics built on an open data platform philosophy.
Primary capabilities
High-speed search, flexible data ingestion, detection rules, and visual investigation tools.
Typical use cases
Technical teams needing customizable analytics across large, diverse data sets.
SolarWinds Security Event Manager
Platform focus
Log and event management focused on infrastructure and operational security visibility.
Primary capabilities
Event correlation, real-time alerts, log analysis, and basic response automation.
Typical use cases
IT-centric security teams managing on-premises infrastructure and operational security needs.
ManageEngine ADAudit Plus
Platform focus
Identity and access monitoring centered on directory services and user activity.
Primary capabilities
User change tracking, access auditing, alerting, and reporting for identity systems.
Typical use cases
Organizations prioritizing identity governance, access monitoring, and audit readiness.
Exabeam Fusion
Platform focus
Unified security operations combining SIEM, automation, and investigation in a single workflow.
Primary capabilities
Behavior analytics, automated playbooks, case management, and guided response.
Typical use cases
SOC teams seeking tighter integration between detection, investigation, and response processes.
OpenText Enterprise Security Manager
Platform focus
Log-centric SIEM with structured correlation and long-term data retention.
Primary capabilities
Event normalization, correlation rules, investigation tools, and compliance reporting.
Typical use cases
Large organizations with established SOC processes and long data retention requirements.
Sumo Logic SaaS Log Analytics
Platform focus
Cloud-native analytics platform with security monitoring as a core use case.
Primary capabilities
Scalable log analytics, detection rules, dashboards, and cloud workload visibility.
Typical use cases
Cloud-first organizations managing distributed applications and services.
Graylog Security
Platform focus
Open and extensible log analysis platform with security-focused capabilities.
Primary capabilities
Log aggregation, search, alerting, and customizable security content.
Typical use cases
Organizations seeking flexible, self-managed log and security analytics solutions.
AT&T Cybersecurity SIEM
Platform focus
Network-informed security monitoring influenced by telecommunications-scale environments.
Primary capabilities
Event correlation, network visibility, threat detection, and investigation workflows.
Typical use cases
Enterprises with complex networks and high-volume traffic analysis needs.
Devo Security Analytics Platform
Platform focus
High-performance analytics designed for real-time visibility across massive data volumes.
Primary capabilities
Fast data ingestion, long-term retention, correlation, and interactive investigation tools.
Typical use cases
Large SOCs handling high event volumes and requiring rapid investigative search.
This appendix provides a neutral snapshot of how widely recognized SIEM platforms are commonly positioned and used, highlighting the diversity of approaches within modern security operations.


